TCP-IP Model Application Layer Protocols
TCP-IP Model Application Layer Protocols
Hello Legendary people! Welcome, In this article, I will examine the application layer in the TCP-IP model in more detail and try to give information about the protocols in this layer.
I mentioned the TCP-IP model before. If you have no idea about this subject, you can learn about it in detail here. TCP-IP model consists of 4 layers. The top layer of these is the application layer. As with every layer, there are protocols specific to this layer. The application layer protocols I found are as follows:
- DNS
- HTTP and HTTPS
- FTP
- SMTP, POP3, IMAP
- SNMP
- TELNET
- SSH
DNS (Domain Name System)
- Domain names are our names on the internet. Each domain has its own unique IP address.
- We use these domain names when we search the internet. This is because it is very difficult and illogical to keep in mind the IP address corresponding to the domains.
- Here DNS is the mechanism that makes Domain-IP address matching for us.
- The reason for this match is that although we use domain names when searching on the Internet, data on the Internet allow us to communicate using IP addresses corresponding to these domain addresses.
- To reach the IP address of a domain, we need to request DNS servers.
- DNS communicates using port 53.
- DNS enables data transmission using UDP.
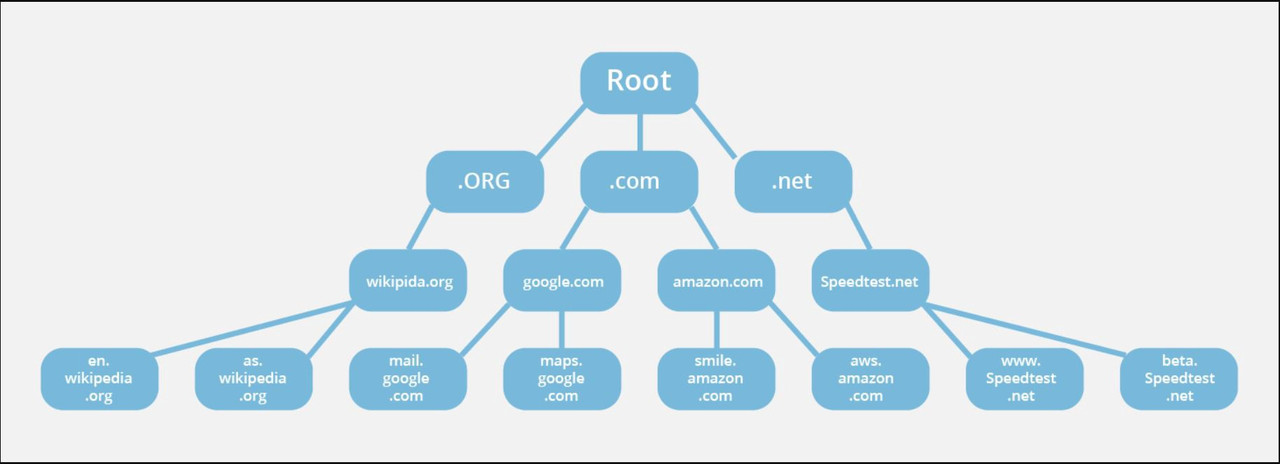
- The structure of DNS is a database that goes from the top to the bottom.
The DNS structure can be summarized as follows:
There are so many details to tell about DNS. But for now, I'm ending it here. Those who want to learn more can find it here.
HTTP (HyperText Transfer Protocol)
- It can also be called Internet communication rules.
- Requests sent from a web page to a server are sent using the HTTP protocol.
- In other words, the information flow between the user and the server is provided by this protocol.
- HTTP request methods can be said as PUT, DELETE, POST and GET.
- HTTP uses port 80.
- HTTPS uses port 443.
- HTTPS is the encrypted form of HTTP.
- It works using TCP.
HTTP responses are:
- 1xx Information messages
- 2xx Successful
- 3xx Redirection
- 4xx Client error
- 5xx Server error
FTP (File Transfer Protocol)
- It is a file transfer protocol.
- It is used to transfer files between two or more computers.
- For this, we need the IP address of the remote computer, FTP software, and the username and password of the account from which we will access the file.
- To use FTP, it is necessary to have a command of FTP commands.
- It is a UNIX-based protocol.
- The commands we use are transferred over another port, the data of the transferred files are transferred over another port.
- Data is transferred from port 20.
- Commands are transmitted from port 21.
- FTP allows sending data using TCP.
SMTP — POP3 — IMAP
- SMTP = Simple Mail Transfer Protocol
- All of these protocols are protocols used for mail transfer.
- SMTP is not used to read emails, but to transmit mails between mail servers.
- We also use POP3 and IMAP to receive and read our emails.
- SMTP uses the TCP protocol.
- SMTP works on port 25.
- We can use IMAP or POP3 to receive or read mail.
- POP3 uses port 110.
- IMAP uses port 143.
- Of course, these ports are the ports that send data without encryption. There are also port numbers that send data by encrypting it.
The picture illustrates very well where these protocols are used.
SNMP (Simple Network Management Protocol)
- It is a network management protocol.
- We can obtain information about devices (switches, routers, printers, etc.) connected to the Internet.
- Data is transferred using UDP packets.
- It is connected using port 161.
Three basic components make up SNMP:
- agent application
- Admin application
- Network management information unit (MIB)
TELNET
- It is an application layer protocol that allows the user to interact with a remote computer.
- It is frequently used by network administrators to access remote devices or devices.
- Telnet uses port 23.
- TCP connection is used.
- The most important issue is that the data is sent unencrypted. An attacker monitoring the network clearly sees the data.
SSH
- This protocol is also used to interact with a remote device, just like telnet.
- Data is sent in an encrypted form.
- Nowadays, SSH is more preferred over Telnet. This is to ensure data security.
- SSH uses port 22.
Yes, in this article, I collected the information that I had researched and found before and tried to write it most understandably for you.
Thank you to everyone who reads and I wish you a healthy day...



Post a Comment